Companies of all types and sizes are in need to protect their critical data assets against breaches and intrusions. Accordingly, companies nowadays, are outsourcing managed security services providers to improve competency, demonstrate security impact and value, and reduce the complexity.

With Ceitcon managed security, you’re able to focus on strategic security priorities, as we manage the day-to-day threat, data protection, and ongoing compliance requirements.
Ceitcon Managed Security Services offers around-the-clock monitoring, manages the day-to-day threat management, and response to advanced threats ,data protection, and ongoing compliance requirements.

Delivers 24x7 administration, monitoring and maintenance of client firewall infrastructure to preserve availability, integrity and privacy of information and defend against threats.


Provides 24x7 monitoring, maintenance and administration of IDS/IPS technology to eliminate malicious traffic with powerful countermeasures.
Delivers 24x7 full lifecycle administration, management and maintenance of log collection technologies enhanced with compliance reporting, providing alerts on real security events.
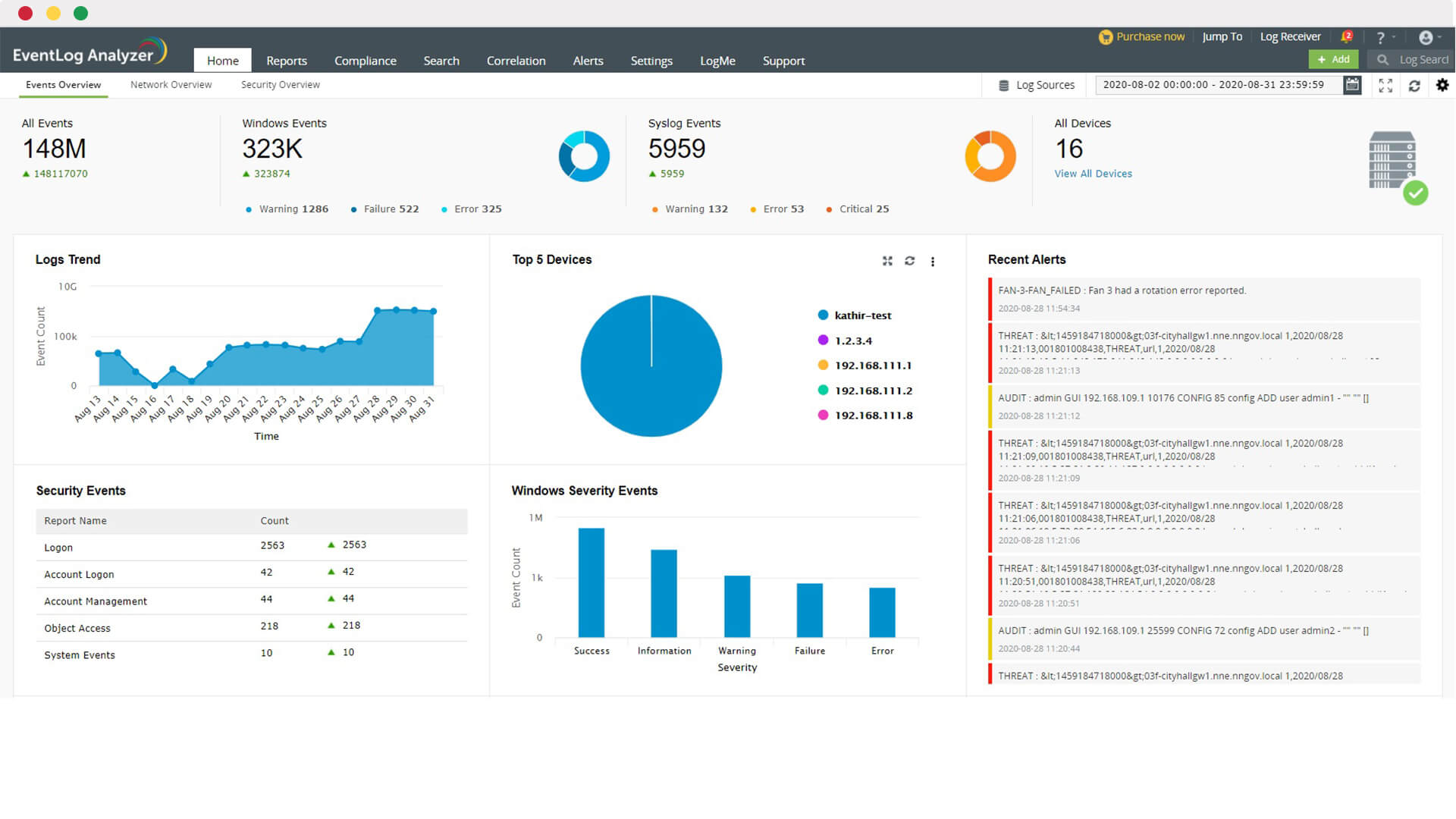

Delivers 24x7 real-time monitoring, correlation and expert analysis of security activity occurring in your environment, driven by our intelligence platform and expert security analysts.
Delivers 24x7 real-time monitoring for all VPN users and their policies that includes, group policies, RADIUS logs, TACAS+ Identity Management, users and password repositories logs.
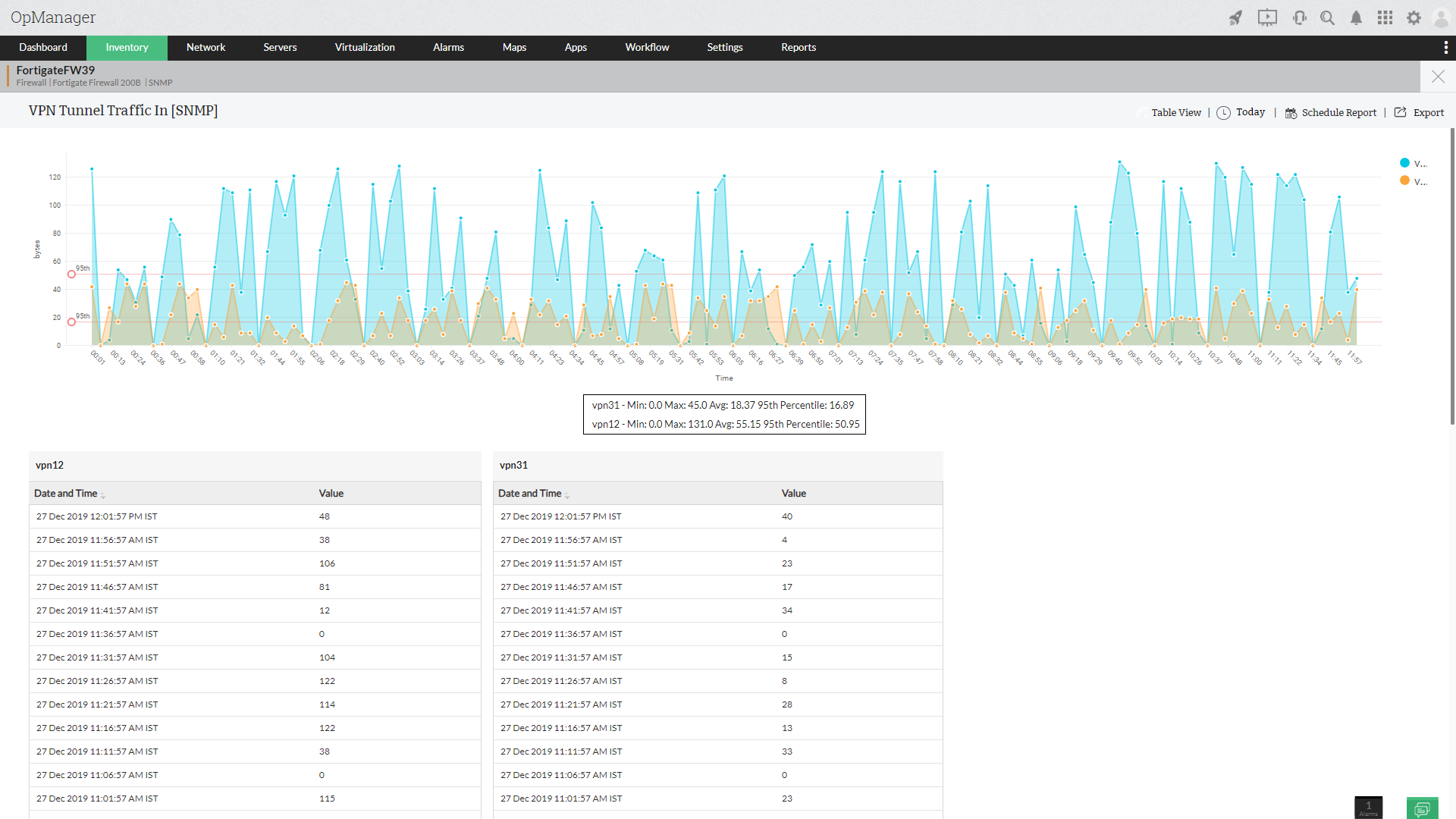

Delivers 24x7 real-time monitoring for operating systems, databases, Business Applications, LDAP and Active Directory systems.
Our team will work closely with your in-house information security function to provide skilled resources throughout the operations commence, our remote 24x7 security monitoring, advanced monitoring and response services.


Process Managing a SOC in a clear and well defined manner is crucial for its success. We will work closely with you to bring our proven SOC management processes to your environment and tailor them to your organization’s needs, where necessary.
Rapidly identify and limit the impact of security threats and risks with 24/7 threat monitoring, detection and targeted response, powered by real-time log analytics, with security orchestration, automation & response tooling for investigation, threat hunting and response. Combine threat intelligence and human expertise for advanced analytics and contextualized events.

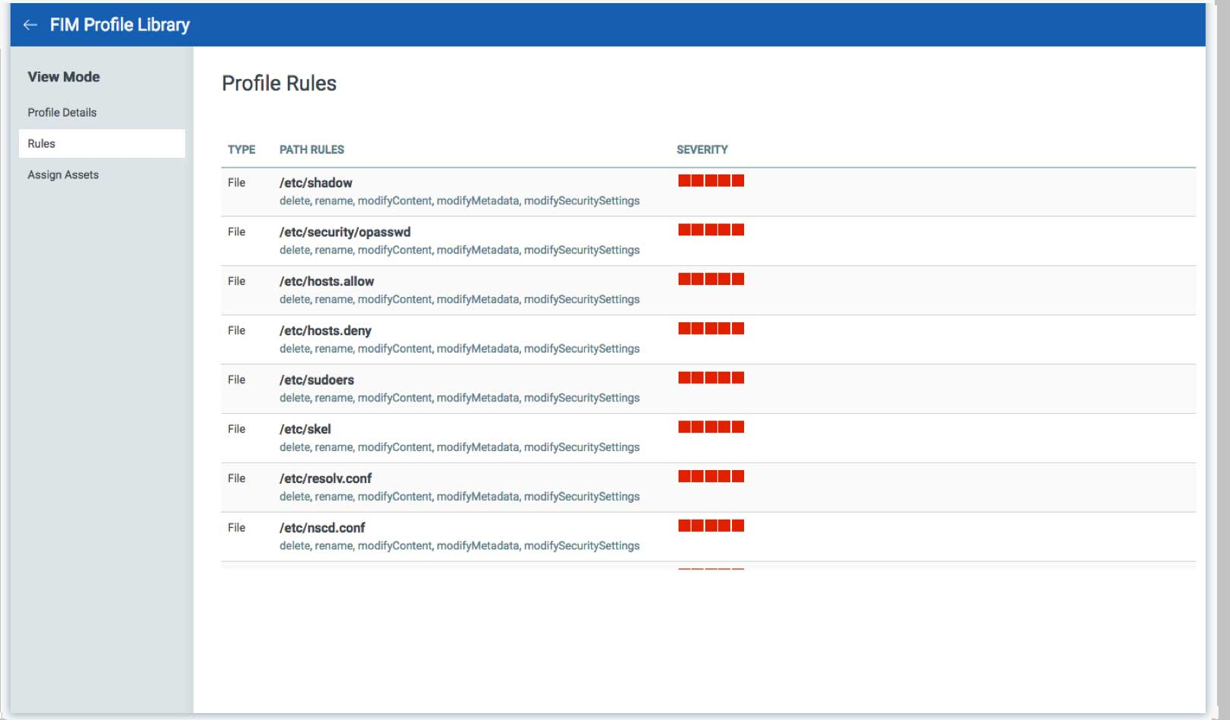
Through the use of Privileged Access Management File Systems event logs shall be monitored for an efficient breach detection method.
Your Ticket Created Successfully
