Ceitcon Security Incident & Event Management (CSIEM) is an enterprise-ready security monitoring solution for threat detection, integrity monitoring, incident response and compliance.
Ceitcon Security Incident & Event Management (CSIEM) is a security solution capable of monitoring your infrastructure, detecting threats, intrusion attempts, system anomalies, poorly configured applications and unauthorized user actions. It also provides a framework for incident response and regulatory compliance.
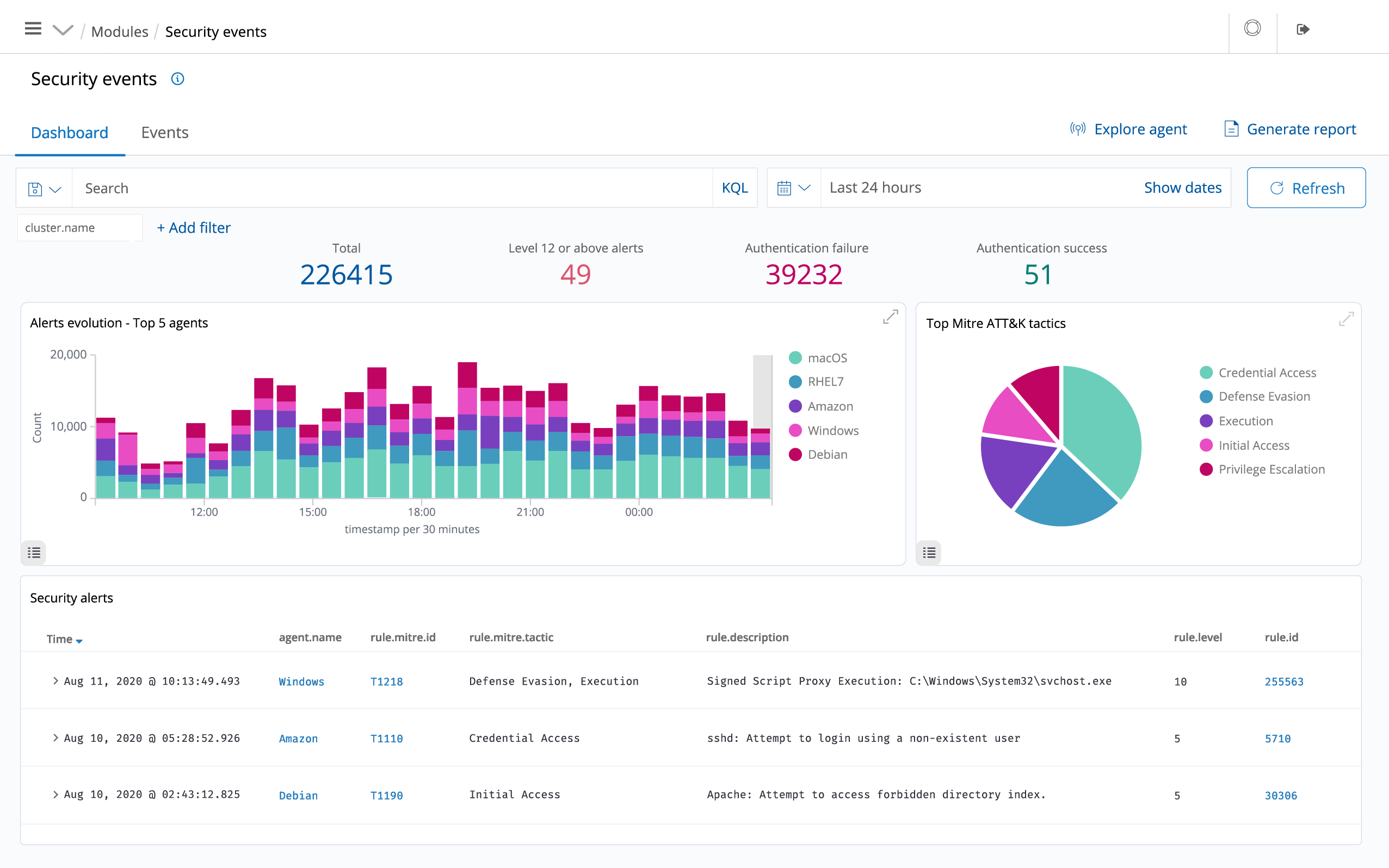
CSIEM is used to collect, aggregate, index and analyse security data, helping organizations detect intrusions, threats and behavioural anomalies.
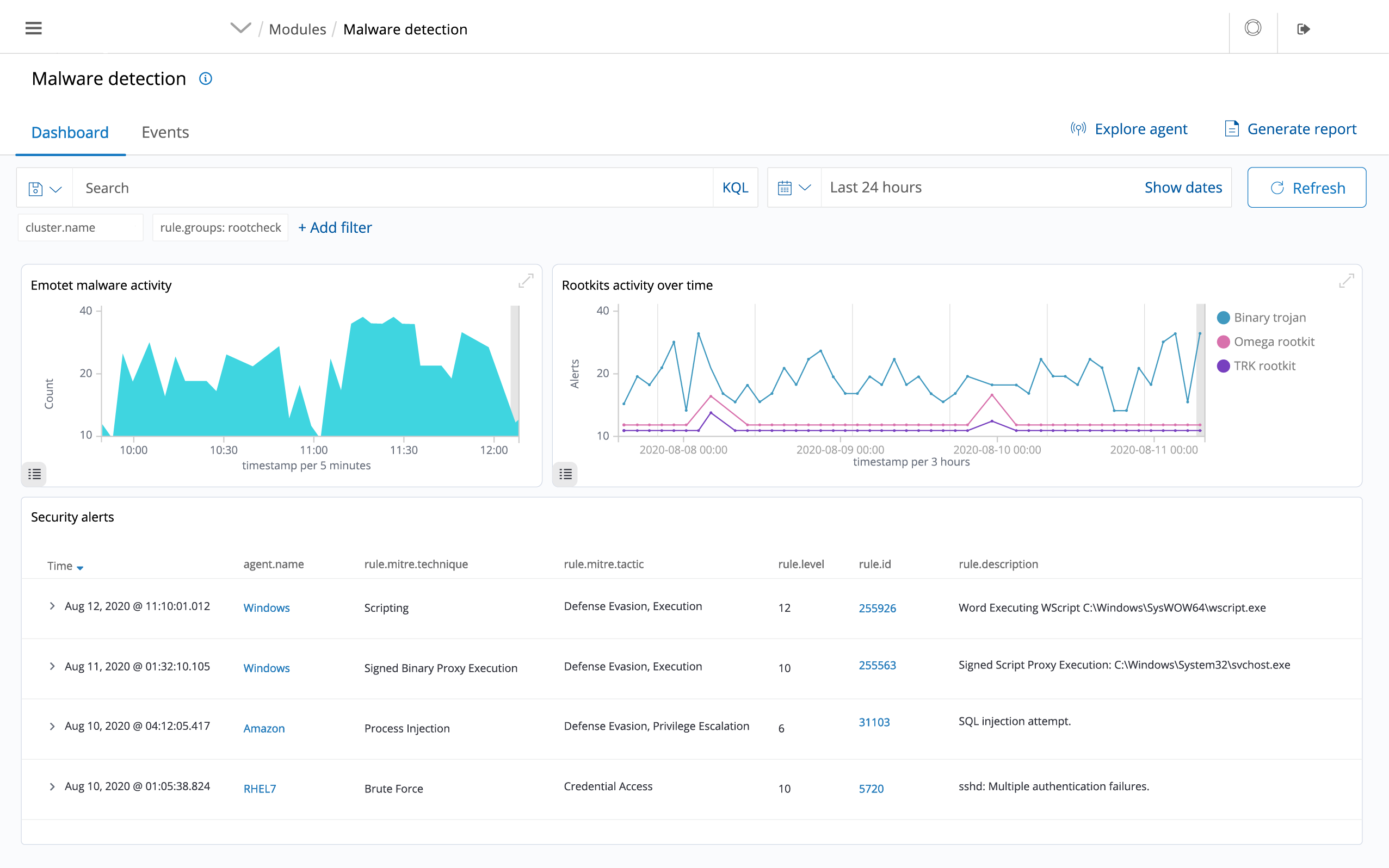
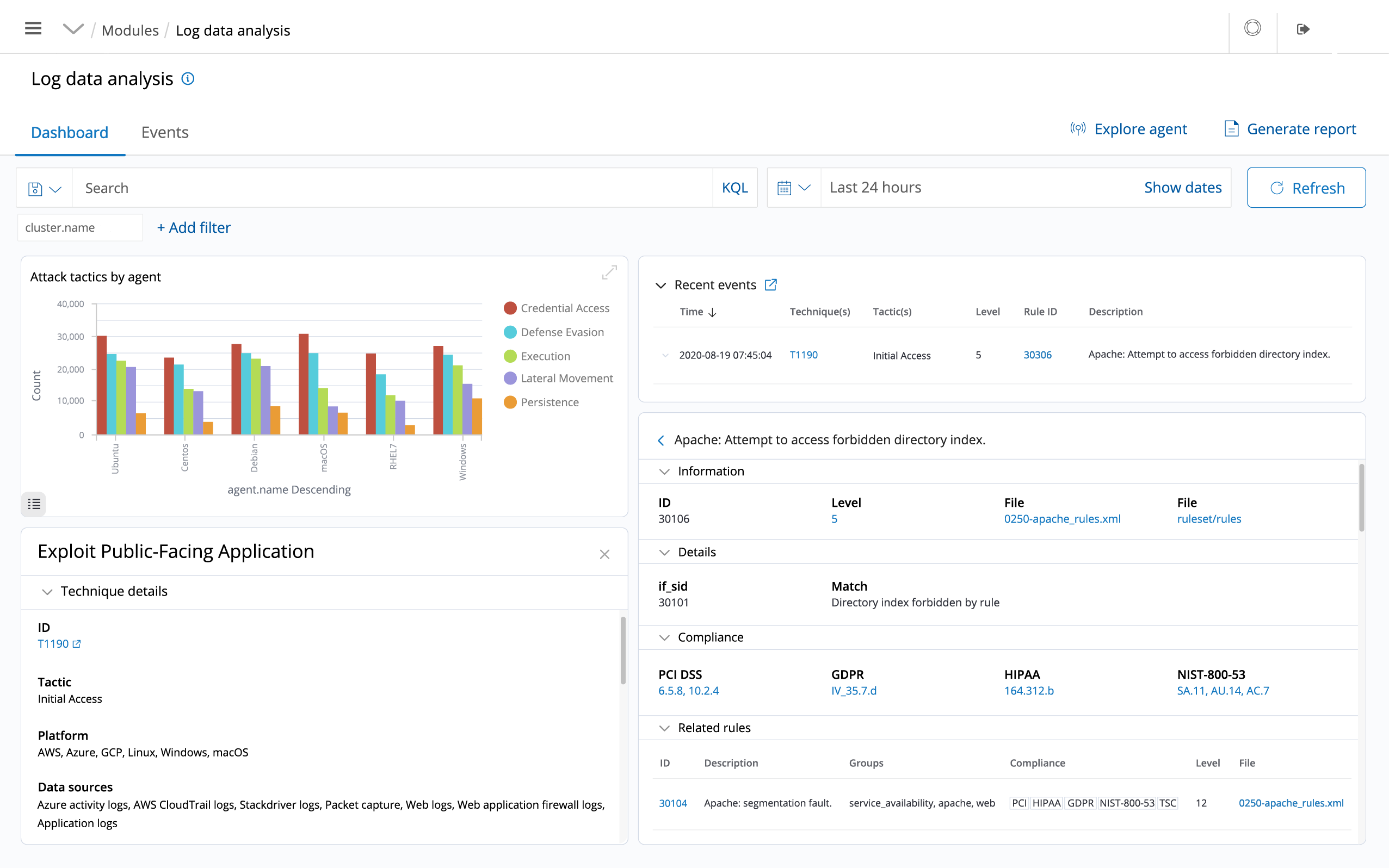
CSIEM scan the monitored systems looking for malware, rootkits and suspicious anomalies. They can detect hidden files, cloaked processes or unregistered network listeners, as well as inconsistencies in system call responses.
CSIEM read operating system and application logs, and securely forward them to a central manager for rule-based analysis and storage.
CSIEM rules help make you aware of application or system errors, misconfigurations, attempted and/or successful malicious activities, policy violations and a variety of other security and operational issues.
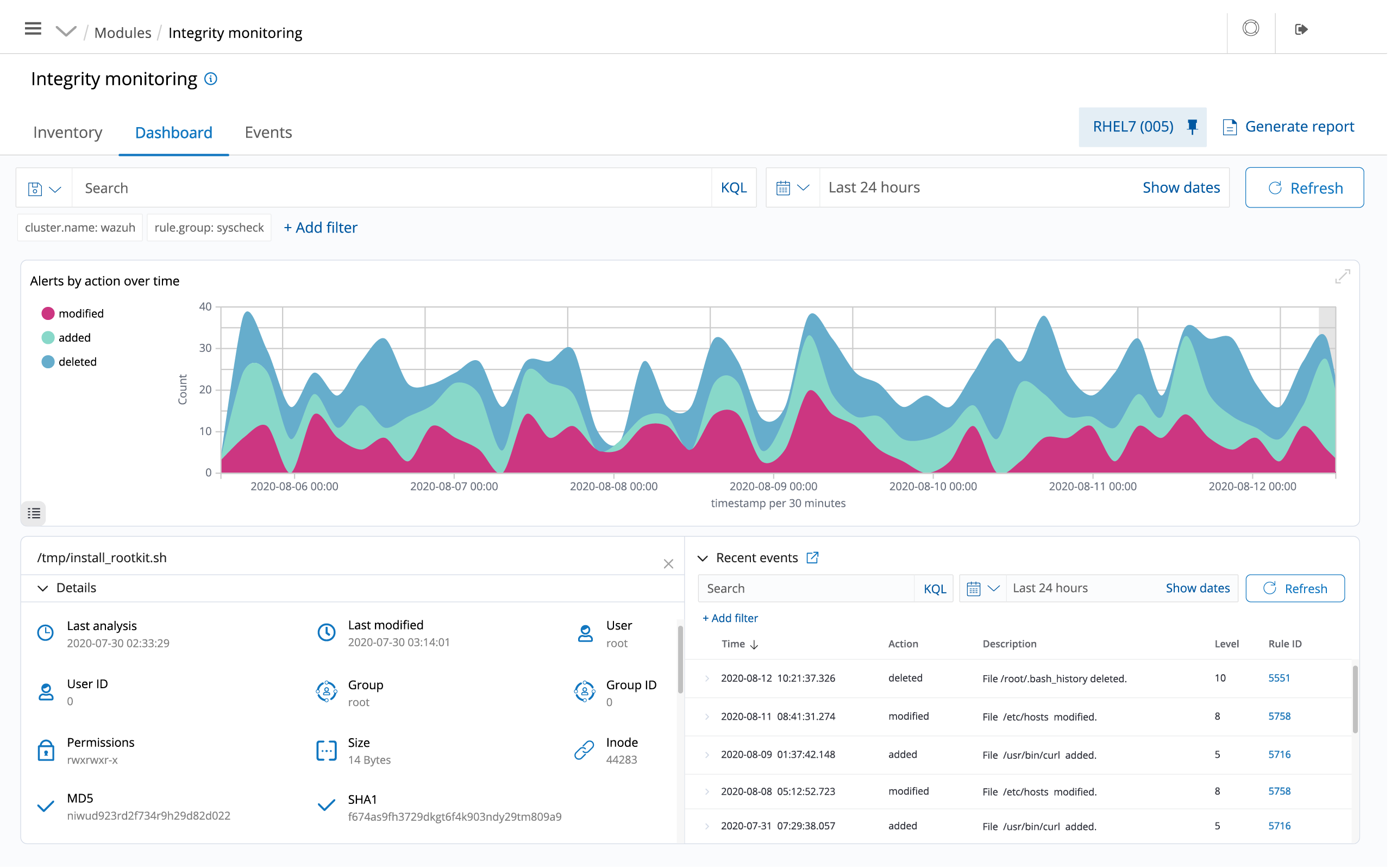
CSIEM monitors the file system, identifying changes in content, permissions, ownership, and attributes of files that you need to keep an eye on. In addition, it natively identifies users and applications used to create or modify files.
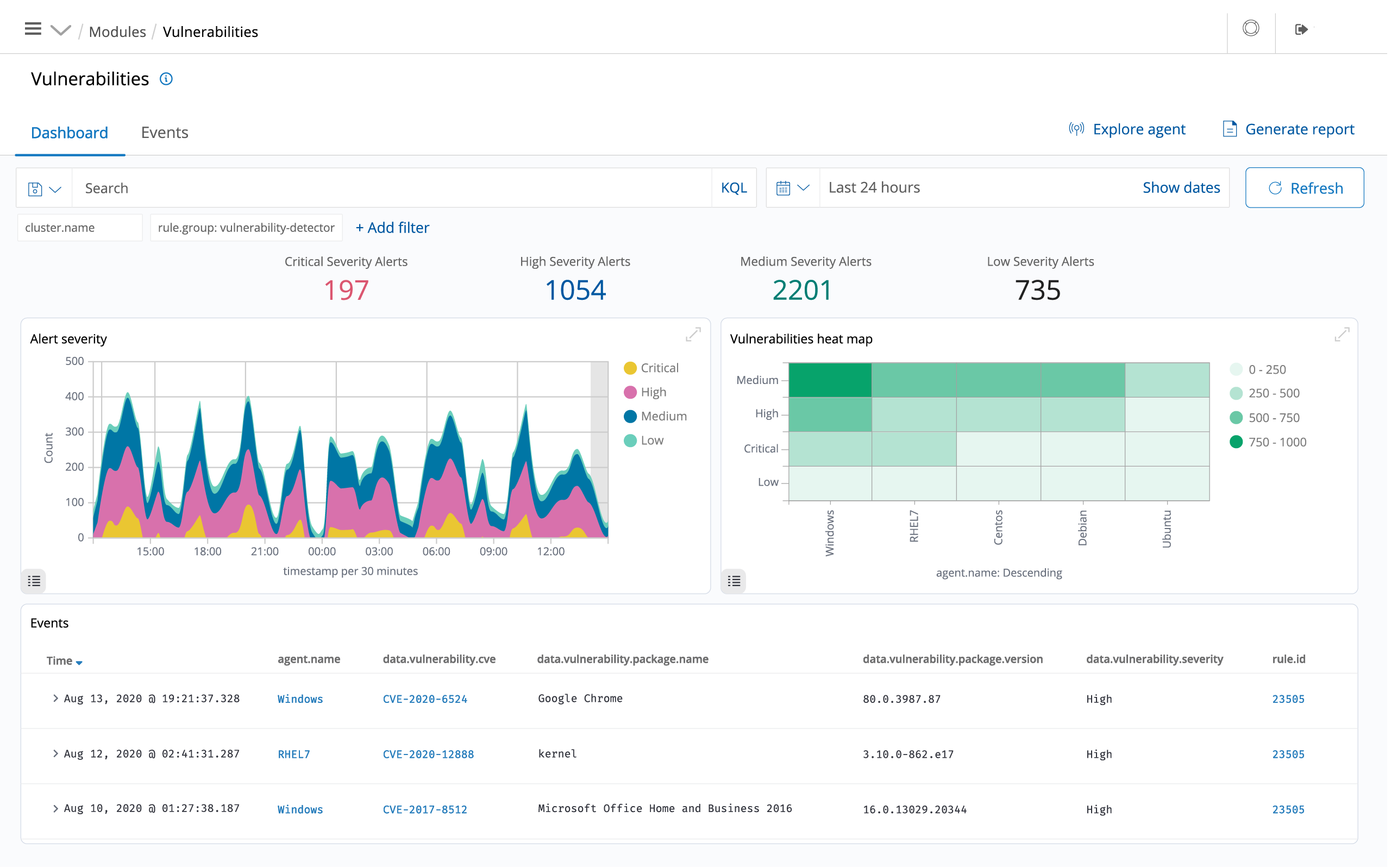
CSIEM pull software inventory data and send this information to the server, where it is correlated with continuously updated CVE (Common Vulnerabilities and Exposure) databases, in order to identify well-known vulnerable software.
Automated vulnerability assessment helps you find the weak spots in your critical assets and take corrective action before attackers exploit them to sabotage your business or steal confidential data.
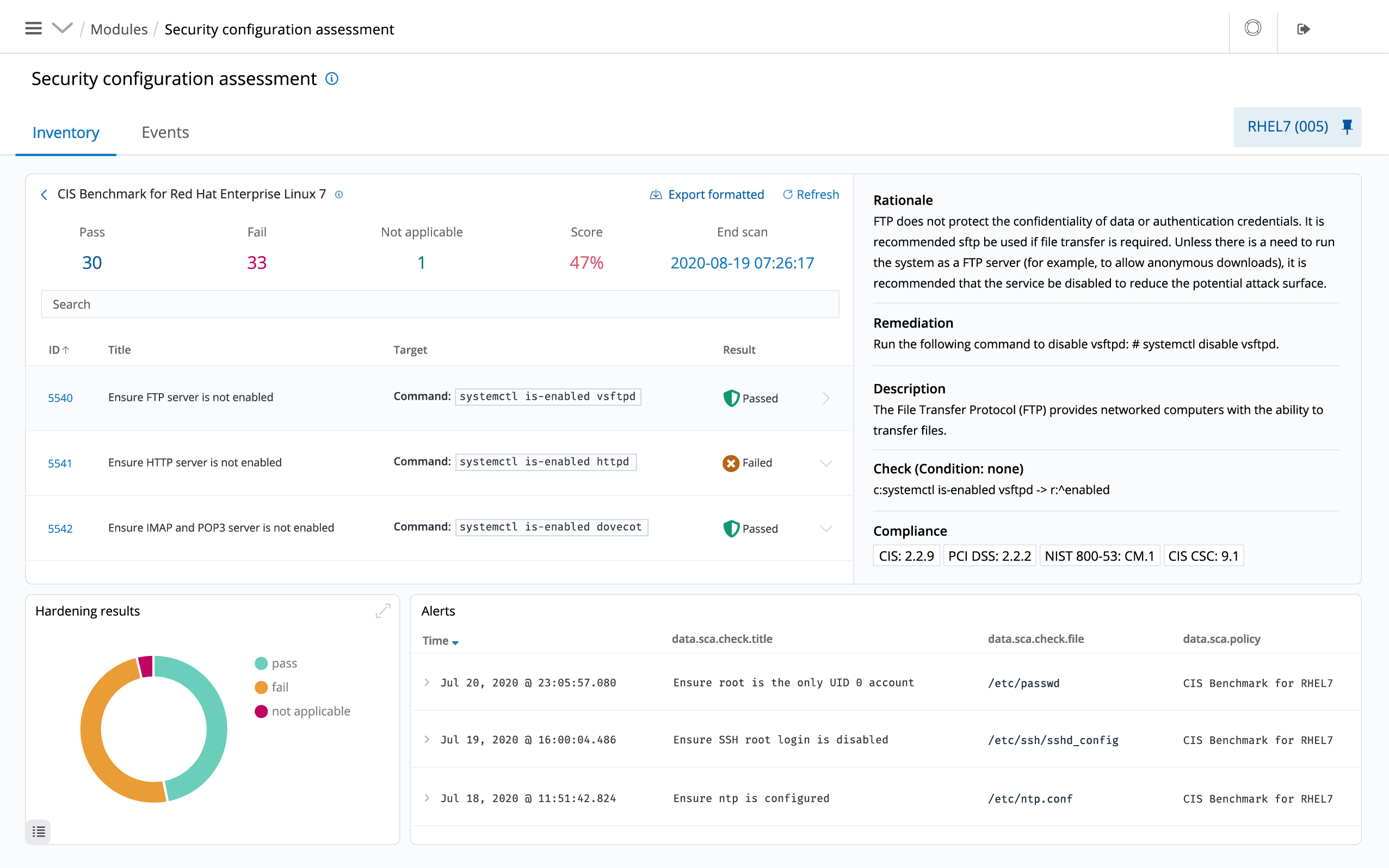
CSIEM monitors system and application configuration settings to ensure they are compliant with your security policies, standards and/or hardening guides. Agents perform periodic scans to detect applications that are known to be vulnerable, unpatched, or insecurely configured.
CSIEM provides out-of-the-box active responses to perform various countermeasures to address active threats, such as blocking access to a system from the threat source when certain criteria are met.
In addition, CSIEM can be used to remotely run commands or system queries, identifying indicators of compromise (IOCs) and helping perform other live forensics or incident response tasks.
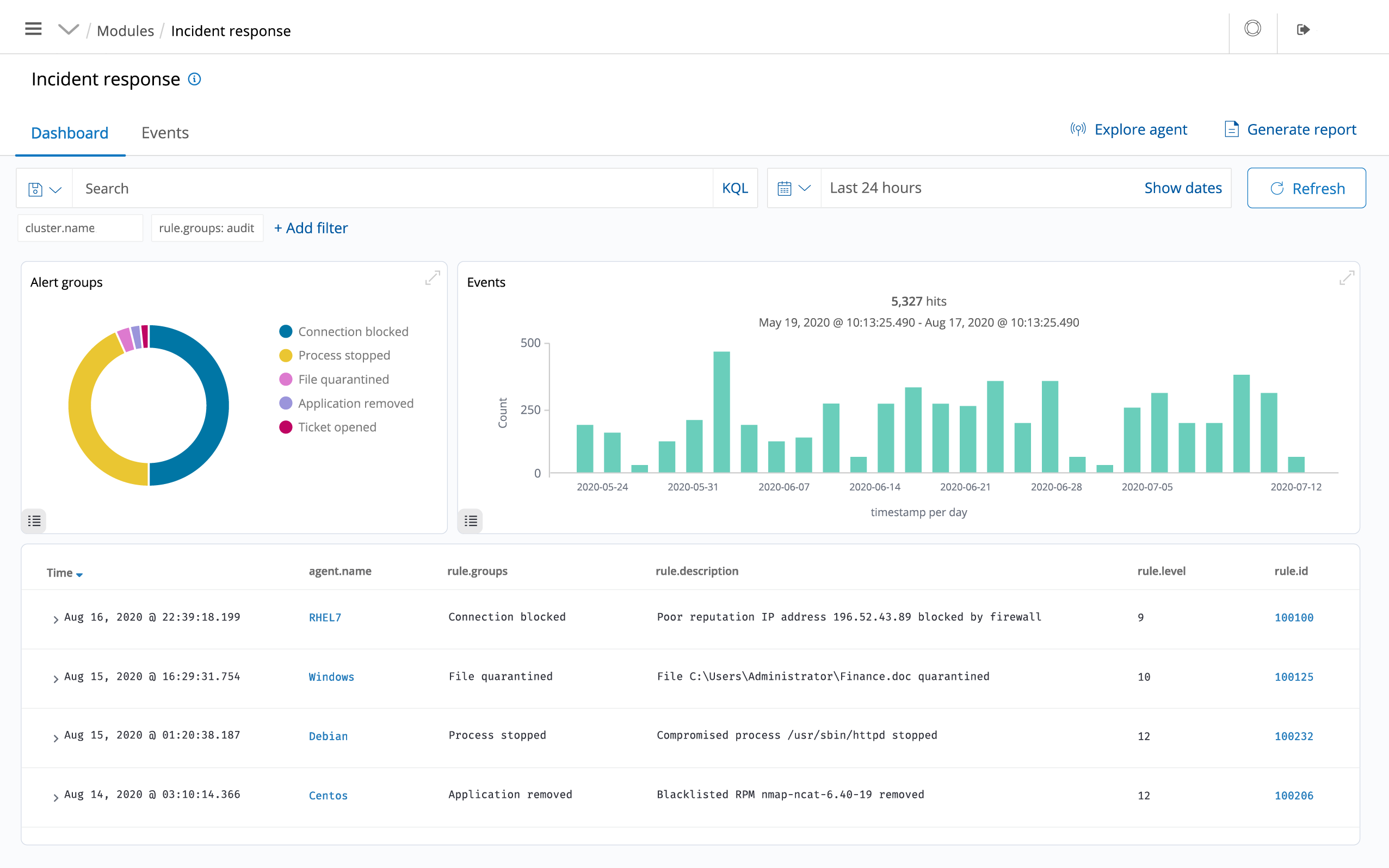
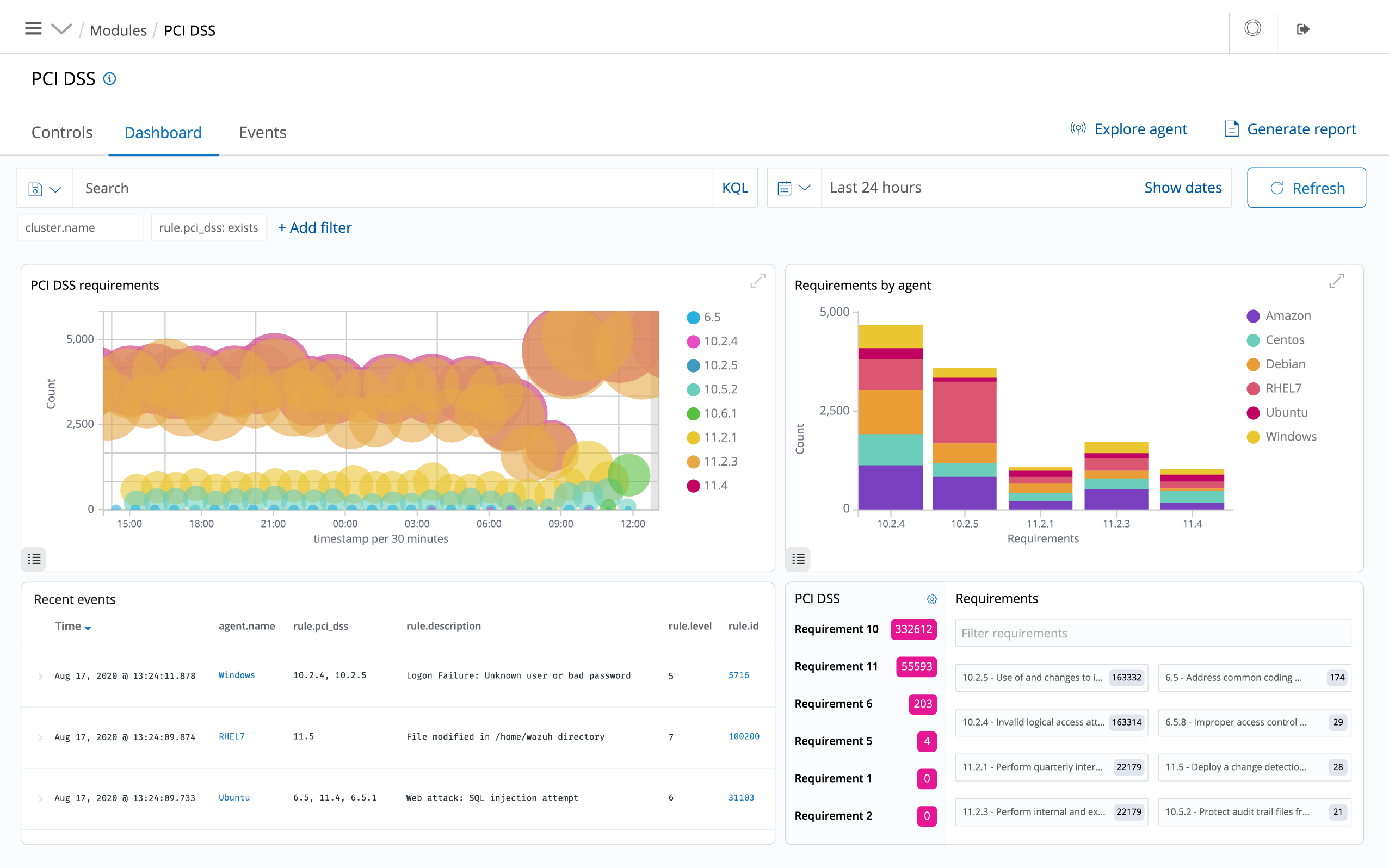
CSIEM provides some of the necessary security controls to become compliant with industry standards and regulations. These features, combined with its scalability and multi-platform support help organizations meet technical compliance requirements.
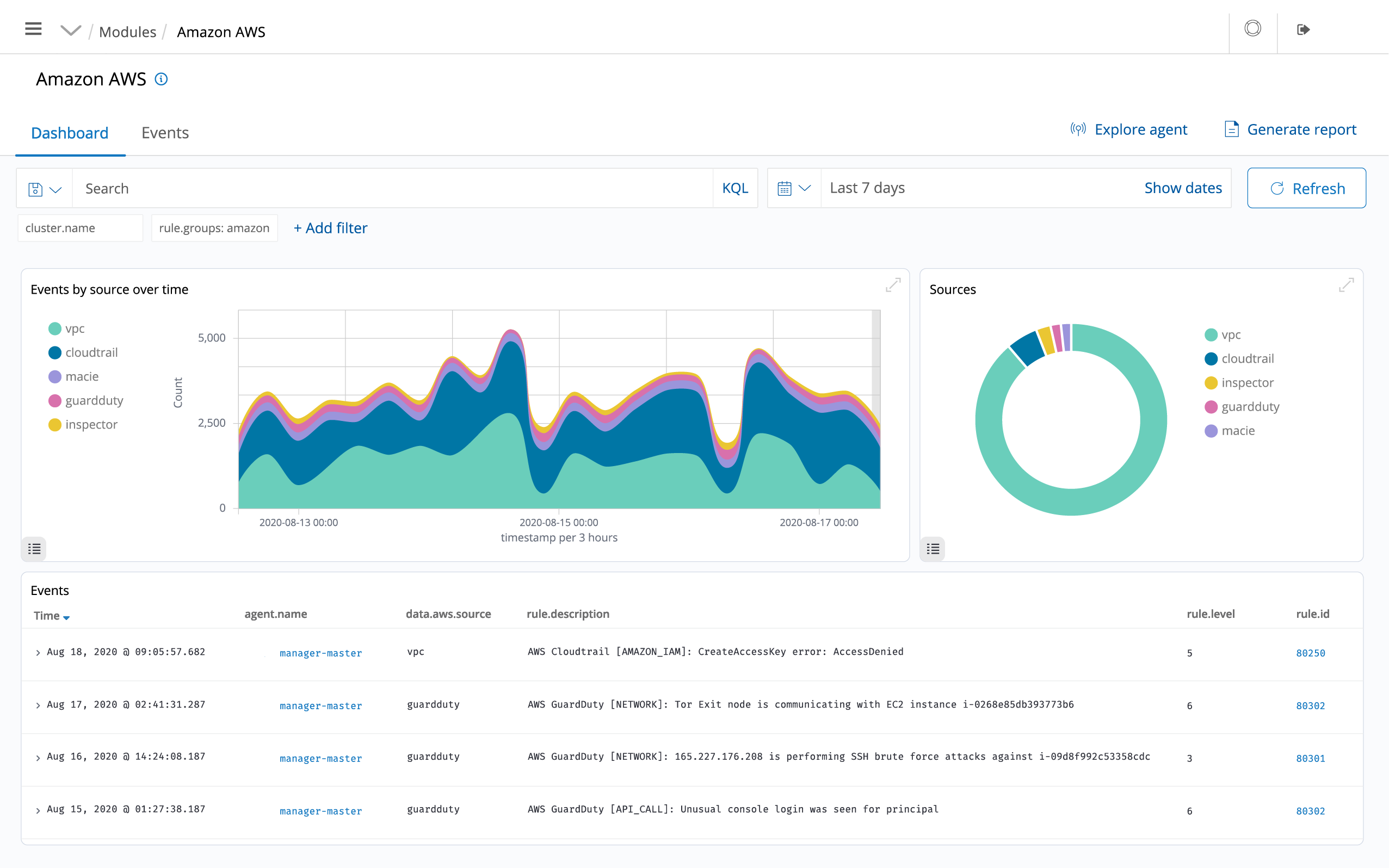
CSIEM helps monitoring cloud infrastructure at an API level, using integration modules that are able to pull security data from well known cloud providers, such as Amazon AWS, Azure or Google Cloud. In addition, CSIEM provides rules to assess the configuration of your cloud environment, easily spotting weaknesses.
In addition, CSIEM light-weight and multi-platform agents are commonly used to monitor cloud environments at the instance level.
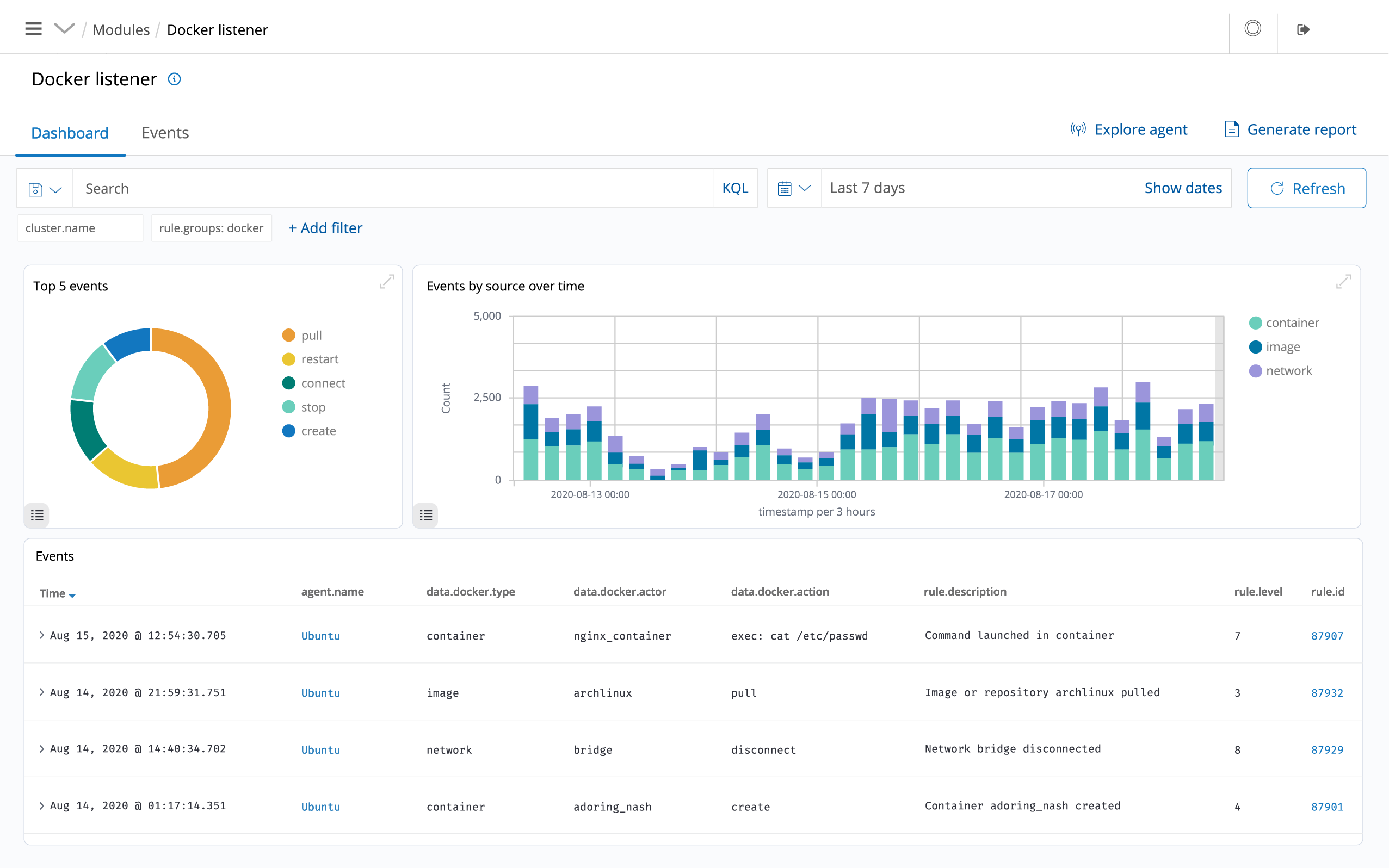
CSIEM provides security visibility into your Docker hosts and containers, monitoring their behavior and detecting threats, vulnerabilities and anomalies. The CSIEM agent has native integration with the Docker engine allowing users to monitor images, volumes, network settings, and running containers.
Your Ticket Created Successfully
